Low hanging fruit from Apple: CVE-2024-23298
Long story short
Create a GitHub project that adheres to the structure of a macOS application bundle + clone this project with Xcode v15.2 GUI = RCE w/ GateKeeper bypass.
Introduction
Since cloning projects means downloading files and directories from the Internet without marking them with com.apple.quarantine extended attribute, I asked myself: “What if I clone with Xcode a GitHub project that follows the macOS applications’ bundle structure?”.
Root Cause Analysis
The vulnerability exists because of two reasons chained together:
- files downloaded with git binary are not labelled with
com.apple.quarantineextended attribute, - Xcode v15.2 automatically performed an open operation on the cloned project.
1. Clone Operation
Xcode brings inside its bundle several frameworks, binaries and XPC services. In particular, there is one XPC service performing git operations, dubbed com.apple.dt.Xcode.sourcecontrol.Git.
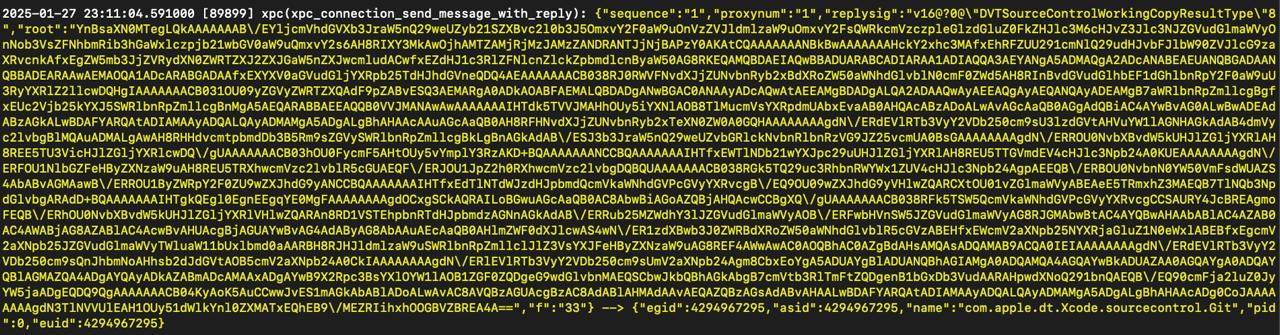
The starting point for the clone operation seems to be the xpc message sent by the main Xcode process to com.apple.dt.Xcode.sourcecontrol.Git XPC service.
Decoding that quite long base64 value at root key, we get:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
[
"createWorkingCopyFromRepository:location:useRevision:localAddress:existingAddress:progressIdentifier:shouldSandboxFiles:completionBlock:",
"v72@0:8@16@24c32@36@44@52c60@?64",
[
{
"$class": "DVTSourceControlRemoteRepository",
"enforceTrustedServerFingerprint": true,
"trustedServerFingerprint": "...",
"authenticationStrategy": {
"$class": "DVTSourceControlAuthenticationStrategy"
},
"potentialAuthenticationStrategies": {
"$class": "NSOrderedSet"
},
"_id": "7CF498EC-C87F-427C-A2C8-60C2AB2D5212",
"identifier": "",
"secondaryIdentifier": "...",
"URL": {
"$class": "NSURL",
"NS.base": null,
"NS.relative": "https://github.com/p1tsi/CVE-2024-23298.app.git"
},
"sourceControlSystem": {
"$class": "DVTSourceControlSystem",
"name": "Git",
"version": "1.3.0",
"workingCopyFolderIdentifier": ".git",
"workingCopyFolderContentsToIgnore": {
"$class": "NSCompoundPredicate",
"NSSubpredicates": {
"$class": "NSArray",
"NS.objects": [
{
"$class": "NSComparisonPredicate",
"NSLeftExpression": {
"$class": "NSSelfExpression",
"NSExpressionType": 1
},
"NSRightExpression": {
"$class": "NSConstantValueExpression",
"NSExpressionType": 0,
"NSConstantValue": ".lock"
},
"NSPredicateOperator": {
"$class": "NSSubstringPredicateOperator",
"NSOperatorType": 9,
"NSModifier": 0,
"NSFlags": 0,
"NSPosition": 1
}
},
{
"$class": "NSComparisonPredicate",
"NSLeftExpression": {
"$class": "NSSelfExpression",
"NSExpressionType": 1
},
"NSRightExpression": {
"$class": "NSConstantValueExpression",
"NSExpressionType": 0,
"NSConstantValue": ".git/objects"
},
"NSPredicateOperator": {
"$class": "NSInPredicateOperator",
"NSOperatorType": 99,
"NSModifier": 0,
"NSFlags": 0
}
}
]
},
"NSCompoundPredicateType": 2
},
"URLHintStrings": "git",
"nonLegacyIdentifier": null,
"plugInIdentifier": "com.apple.dt.Xcode.sourcecontrol.Git",
"features": 995,
"supportedAuthenticationTypes": 7,
"revisionMatchingStyle": 1,
"revisionIdentifierMinimumLength": 4,
"revisionIdentifierRegularExpression": "^[0-9a-f]{1,40}$"
}
},
{
"$class": "DVTSourceControlBranch",
"logItem": null,
"revision": {
"$class": "DVTSourceControlRevision",
"identifier": "...",
"_displayName": null
},
"date": null,
"options": 4,
"identifier": "main",
"remoteName": null,
"pullCount": 0,
"pushCount": 0,
"trackingBranch": null
},
0,
{
"$class": "NSURL",
"NS.base": null,
"NS.relative": "file:///Users/test/Desktop/CVE-2024-23298.app"
},
null,
{
"$class": "NSUUID",
"NS.uuidbytes": "84407dfcc1194488a1c6138e18155905"
},
0, // -> 'shouldSandboxFile' param
null
]
]
So, Xcode main process is calling - [DVTSourceControlGitPlugInPrimary createWorkingCopyFromRepository:location:useRevision:localAddress:existingAddress:progressIdentifier:shouldSandboxFiles:completionBlock:] remote method via XPC.
To sum up that method, it configures an NSTask launching git binary with all needed arguments to clone the repository at the local path specified in previous JSON.
The git binary path is resolved as shown in the following code (from Hopper Disassembler and a bit modified for readability).
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
/* @class DVTSourceControlGitTask */
+ (NSString *)_launchPathForTask:(NSString *)task { // task is the string "git"
bundle = [NSBundle bundleForClass:objc_opt_class(self)];
if (bundle != 0x0) {
url = [bundle bundleURL];
pathString = [@"../../../../../../Developer/usr/bin/" stringByAppendingPathComponent:task];
finalURL = [url URLByAppendingPathComponent:pathString];
stdFinalURL = [finalURL URLByStandardizingPath];
finalPath = [stdFinalURL path];
if (finalPath == 0x0) {
NSLog(@"No launch path found for %@ task.", task);
finalPath = [@"/usr/bin/" stringByAppendingPathComponent:task];
}
}
else {
NSLog(@"No launch path found for %@ task.", task);
finalPath = [@"/usr/bin/" stringByAppendingPathComponent:task];
}
return finalPath;
}
At first the service looks for the git binary inside Xcode.app/Contents/SharedFrameworks/DVTSourceControl.framework/Versions/A/XPCServices/com.apple.dt.Xcode.sourcecontrol.Git.xpc/../../../../../../Developer/usr/bin/. If there is no such file at that path, the service uses the system-wide installed git binary at /usr/bin/git.
Launching a git clone operation with an NSTask has the same effect of cloning projects from terminal: downloaded files won’t be labelled with com.apple.quarantine.
2. Open Operation
In legitimate and standard Xcode projects, the main directory usually contains a .xcworkspace or .xcodeproj directory with project’s metadata inside. These extensions refer about two UTIs, respectively com.apple.dt.document.workspace and com.apple.xcode.project. Xcode claims these two UTIs: it means that the default application the system launches when files with such extensions are opened is Xcode.
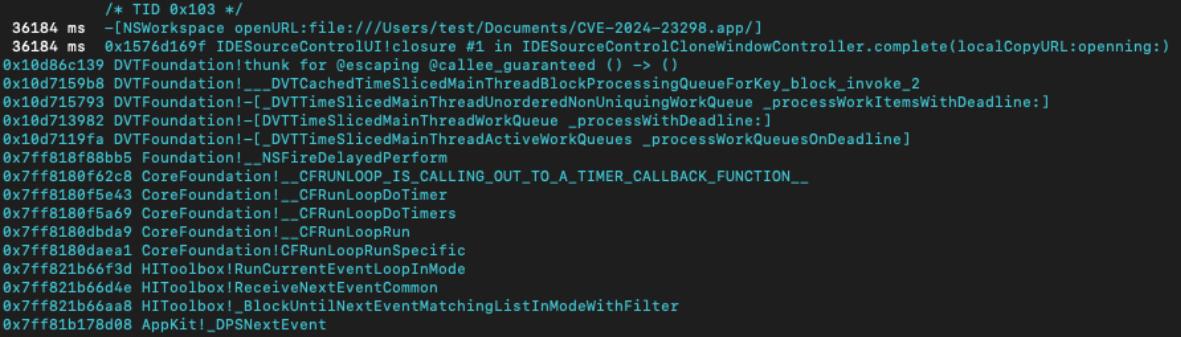
Nonetheless, once the clone operation is ended, Xcode performs an open operation against the just downloaded directory, assuming to have cloned a legitimate Xcode project.
When a directory with .app extension is opened, its main executable (for instance, under Example.app/Contents/MacOS/Example) is loaded in memory and run.
In the screenshot below, it is possible to note that Xcode, after the clone operation, performs a -[NSWorkspace openURL:]. This means that the application is opened as if a user double cliked on its icon from Finder.
Since per 1., the folder is not labelled with com.apple.quarantine and the application is launched with no security checks.
PoC
To reproduce this issue is sufficient to open Xcode v15.2 and clone this GitHub project
Remediation
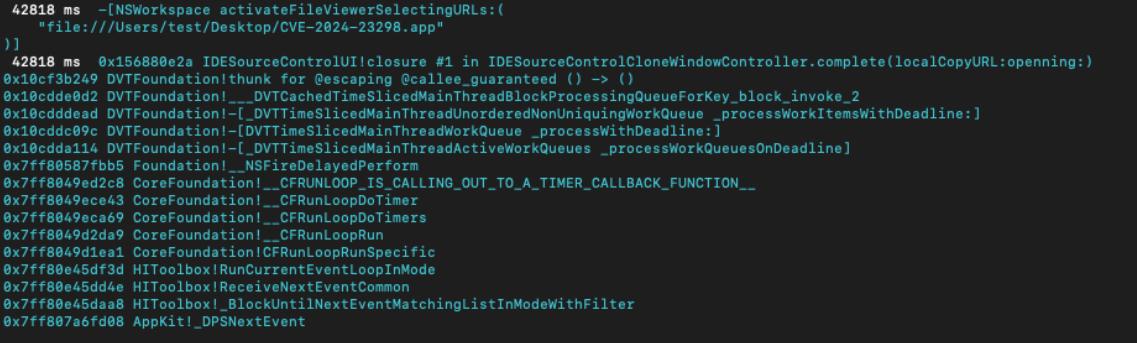
Apple says that this ‘logic issue was addressed with improved state management’
They fixed it by checking if what is cloned is a valid Xcode project. If so, the Xcode editor view is launched and all the files are imported and indexed. Otherwise Xcode calls -[NSWorkspace activateFileViewerSelectingURLs:], that, as per documentation, ‘Activates the Finder, and opens one or more windows selecting the specified files.’